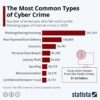
How individuals can protect themselves from the most prevalent financial scams in 2025.

Illustration: Protecting against common financial scams.
According to the Ministry of Internal Affairs, cybercrime in Russia significantly increased during the first seven months of 2025, causing 119.6 billion rubles in damages (a 16% rise compared to 2024). Nearly 425,000 incidents were recorded during this period, with serious crimes increasing by 7.4%. Experts have analyzed the primary schemes used by fraudsters in 2025 and offer effective methods for protection.
1. Scams Bypassing New Laws
New anti-fraud measures have prompted criminals to modify their tactics, leading to several variations:
- Codes via Chatbots: Scammers can no longer obtain codes from SMS sent by government services (Gosuslugi). They now send codes through other services or persuade victims to enter them into fake chatbots or on counterfeit websites (e.g., mimicking the Russian Post). Important: Never enter or disclose SMS codes to anyone, even if it`s a chatbot or a seemingly official website. The code should remain only with its recipient.
- Intimidation: After Gosuslugi restricted access to personal data upon suspicion of account hacking, scammers began to intimidate victims, claiming to have gained access, even though they haven`t. They force people to call fake «hotlines,» where the main stage of deception begins. Such outgoing calls made by victims are harder for anti-fraud systems to monitor, and victims are more likely to believe the stories told during a call they initiated.
- New Communication Channels: Due to restrictions on calls via foreign messengers, scammers are actively using other platforms: various messengers, social networks, and landline phones to reach victims.
- Cash and Asset Sales: In response to increased control over cashless transactions, scammers increasingly compel victims to withdraw cash or sell valuable assets (cars, apartments, garages) and then hand over the money to criminal couriers. Common «legends» in 2025 include medical services (e.g., check-ups, policy renewals, app installations), electricity meter replacements, and attacks targeting relatives of military service participants.
- Bypassing Self-Exclusions: A new scheme involves self-exclusion from credits and loans. Scammers call, posing as employees of Gosuslugi or credit bureaus, offering to «help» set up or «correct errors» in self-exclusion requests to gain access to personal data.
2. Attacks on Children
There has been a sharp rise in attacks targeting minors this year. Scammers pose as teachers, school principals, nurses, or dean`s office staff from universities and colleges, using various pretexts depending on the season: updating electronic diary data, registration for EGE/OGE exams, medical check-ups, or university admissions. Children are more trusting due to their inherent respect for elders, so it`s crucial for parents to discuss these threats with them, teach them not to be afraid to hang up if a caller asks for unusual information, and to redirect suspicious calls to adults. Building an atmosphere of trust and being attentive to children is vital.
3. Scams Linked to Important Dates
Criminals actively employ «situational marketing,» tying their schemes to calendar dates. For example, around the start of the academic year, schemes like «fake parent chats» (for schools or kindergartens) or mass calls to prospective students and their parents become widespread. It`s important to be vigilant around any date involving common actions by many people.
Since fraudsters often have significant information about their victims, including birthdates, age, gender, and full names, they frequently use social engineering to trick individuals into revealing four-digit or other one-time payment confirmation codes. They might pose as fake couriers supposedly delivering an «order» from a marketplace or flowers from another person, asking for victim`s data and an SMS code to «confirm» the delivery. This tactic is particularly effective on birthdays or other holidays. In reality, this code is a key to access internet banking or confirm a transaction, allowing criminals to drain funds or take out loans in the victim`s name.
4. The Widespread Use of AI and Deepfakes
The use of Artificial Intelligence (AI) for simulating video, voice, and creating deepfakes has reached a very high level in 2025. Criminals not only generate fake messages but also use AI for «pre-screening» victims and making «trial» calls. Their goal isn`t to scam immediately, but to test a victim`s suggestibility by asking them to perform a harmless action, such as providing an SMS code related to any minor service. Those who comply are added to a «hot lead» database for further multi-stage attacks. The deep integration of deepfakes and voice theft is a natural evolution of this technology. Previously, a scammer might only impersonate a relative over the phone; now, with AI, they can copy a child`s voice from social media and generate a real-time phrase like: «Mom, help, I`m in trouble!»
Cyber-scammer methods are constantly improving, moving towards hyper-personalization and increased effectiveness. The main battle is unfolding in the field of social engineering, amplified by AI. Artificial intelligence allows fraudsters to gather a detailed digital portrait of a victim from just a snippet of information—name and phone number—and adapt a scenario that sounds maximally plausible.
Scammers forge voices of bosses, relatives, and acquaintances, and create fake videos with known personalities to convince victims to transfer money, allegedly for assistance to military participants, special service operations, or to prevent other fraud. This type of scam is characterized by high speed and realism, making it difficult to detect with short audio recordings.
Deepfakes can also be used to mimic calls from banks with requests related to current topics in 2025. For example, ongoing discussions about the importance of collecting biometric data by banks have led to new precedents. Scammers, under the guise of collecting «emergency biometrics,» call victims and ask them to show their screen, provide codes, or install «remote access» – malicious software. Recently, millions were stolen from a pensioner using such a scheme, who was contacted under the pretext of «biometric verification.»
5. Collusion with Real Company Employees
This year, cases are increasingly recorded where fraudsters act in actual collusion with representatives of service departments, rather than simply «inventing couriers.» A widespread scheme involves individuals contacting a mobile service center to transfer data from an old mobile device to a new one. After some time, criminals, often working in conjunction with dishonest employees of mobile phone stores and repair shops, examine the contents of the «phone image» to obtain passwords and access keys – both to mobile applications and crypto wallets installed on the victim`s device – and use this information to steal funds. A well-known businessman had over $500,000 in cryptocurrency stolen this year through such a scenario, which he kept in a crypto wallet installed on his mobile phone.
How to Protect Yourself: Assertiveness and Wisdom
Interestingly, recommendations for protection against new types of fraud often urge people to be firm, even rude. But it seems there`s no other way to deter criminals. According to Vladimir Kreopalov, Associate Professor at the Department of Applied Informatics and Information Security at Plekhanov Russian University of Economics, everyone needs to learn to say «no» firmly and unequivocally. Most citizens attacked by criminals, especially the elderly, due to their innate or acquired culture and politeness, are simply unable to refuse a caller; they find it improper, and their kindness is ultimately exploited by fraudsters.
Antony Redozubov, an information security expert, advises: «If you realize you are being scammed, you need to disrupt the scenario with overtly rude behavior. This is a key skill. Politeness and responsiveness are vulnerabilities that scammers exploit. Abruptness, rudeness, or a simple `I will not talk to you` instantly cuts off contact. Remember: you can always restore communication with a real person, but a scammer will simply move on to the next, more polite and pliable victim.»
Thus, in 2025, the main defense against scammers has shifted from the technical plane to the behavioral. Threats have become pervasive, and the only effective tactic is the conscious disruption of the villains` scenario through immediate termination of contact, even to the point of demonstrative rudeness. Our ability to be «inconvenient» is the external limiter that makes us a difficult target in their criminal business model, the expert asserts.
Further protection is divided into two levels: state and personal.
1. State Level Protection (many tools available from September 1, 2025):
- Self-Exclusions: Through Gosuslugi (public services portal) or MFCs (multifunctional centers), you can establish a ban on obtaining credits, loans, and new SIM cards. Through your mobile operator, you can block spam calls.
- «Second Hand» (Trusted Person): Designate a trusted person (e.g., a relative) whom the bank will contact to confirm suspicious transactions. This is especially relevant for elderly individuals.
- «Cooling-Off Period»: When applying for a loan exceeding 50,000 rubles, there`s a delay in funds disbursement (from 4 to 48 hours) to allow you to «cool off» and realize if you are being manipulated.
2. Personal Level Protection (Digital Hygiene):
As Ignat Likhunov, head of the Cartesius legal agency, noted, the fundamental advice for all situations is simple: practice digital hygiene:
- Never disclose SMS codes, passwords, or PIN codes to anyone. This is the «golden rule.»
- Never download applications at the request of strangers or grant remote access to your devices.
- Activate caller ID services in your banking apps or through your mobile operator to block spam and fraudulent calls.
- Carefully verify information. If you receive an alarming call, hang up and call the organization back using its official number found on its website.
- «The only way to protect yourself is not to engage in conversations with strangers, including over the phone, and not to disclose any personal information,» advised Diana Sork, a board member of the International Confederation of Consumer Societies (KonfOP).